Picture this: you're sitting on your couch, sipping coffee, and suddenly you need to access your Raspberry Pi from miles away. Sounds impossible? Not anymore! RemoteIoT VPC SSH Raspberry Pi has got your back, making it easier than ever to control your devices remotely while keeping everything secure.
Let’s face it, we live in a world where everything is connected. From smart homes to IoT devices, the demand for remote access is skyrocketing. But here’s the catch—how do you ensure that your setup is not only efficient but also secure? That’s where RemoteIoT VPC SSH Raspberry Pi comes into play. It’s like having a personal assistant that lets you manage your devices without breaking a sweat.
This guide isn’t just about throwing technical jargon at you; it’s about breaking down the complexities of RemoteIoT, VPC, SSH, and Raspberry Pi into bite-sized chunks. By the end of this article, you’ll be equipped with the knowledge to set up your own secure remote access system. So, buckle up and let’s dive in!
Table of Contents
- What is RemoteIoT?
- Understanding VPC
- SSH Basics: What You Need to Know
- Raspberry Pi: The Ultimate Device
- Integrating RemoteIoT, VPC, and SSH
- Securing Your Connection
- Common Issues and Solutions
- Real-World Applications
- Future Trends in RemoteIoT
- Conclusion
What is RemoteIoT?
Alright, let’s start with the basics. RemoteIoT is more than just a buzzword—it’s the backbone of modern connectivity. Imagine being able to control your IoT devices from anywhere in the world. Sounds futuristic, right? Well, it’s here, and it’s real.
RemoteIoT refers to the technology that allows you to access and manage your Internet of Things (IoT) devices remotely. Whether you’re tweaking settings on your smart thermostat or checking the status of your security cameras, RemoteIoT makes it all possible.
But here’s the kicker: it’s not just about convenience. With RemoteIoT, you can ensure that your devices are always up and running, even when you’re not physically present. And when you combine it with VPC and SSH, you’ve got a powerhouse of secure remote access.
Why RemoteIoT Matters
- Enhances device management efficiency
- Provides real-time monitoring and control
- Improves overall system security
Understanding VPC
Now that we’ve covered RemoteIoT, let’s talk about VPC. VPC stands for Virtual Private Cloud, and it’s like having your own private network in the cloud. Think of it as a secure bubble where all your devices can communicate without worrying about prying eyes.
When you set up a VPC, you’re essentially creating a virtual network that mimics a traditional local area network (LAN). But the best part? It’s all hosted in the cloud, which means you can access it from anywhere as long as you have an internet connection.
For Raspberry Pi users, VPC is a game-changer. It allows you to isolate your devices from the public internet, reducing the risk of unauthorized access. And when combined with SSH, it becomes an impenetrable fortress of security.
Key Features of VPC
- Isolated network environment
- Customizable IP addresses
- Advanced security controls
SSH Basics: What You Need to Know
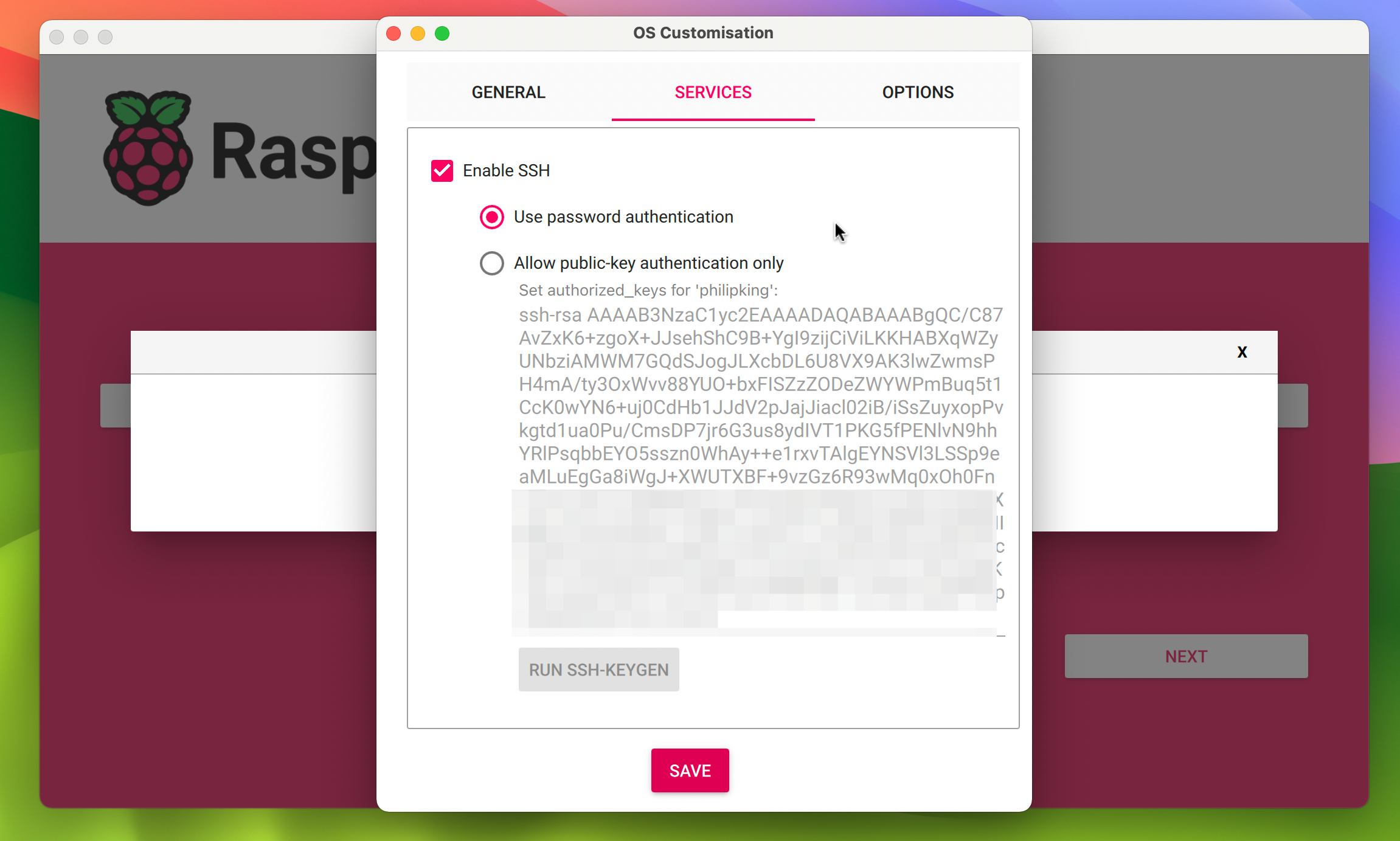
SSH, or Secure Shell, is the unsung hero of remote access. It’s a cryptographic network protocol that allows you to securely connect to your devices over an unsecured network. In simpler terms, SSH is like a secret handshake that ensures only authorized users can access your devices.
For Raspberry Pi enthusiasts, SSH is a must-have tool. It enables you to manage your Pi remotely, whether you’re configuring settings, running scripts, or troubleshooting issues. And the best part? It’s built right into the Raspberry Pi OS, so you don’t need any additional software.
But here’s a pro tip: always use strong passwords and enable two-factor authentication (2FA) to enhance your security. Trust me, you don’t want to be the victim of a brute-force attack.
SSH Commands You Should Know
ssh username@ip_address: Connect to your Raspberry Piscp file.txt username@ip_address:/path/to/destination: Transfer files securelyssh-keygen: Generate SSH keys for passwordless authentication
Raspberry Pi: The Ultimate Device
Let’s talk about the star of the show: the Raspberry Pi. This tiny yet powerful device has revolutionized the world of computing and IoT. Whether you’re a hobbyist or a professional developer, the Raspberry Pi offers endless possibilities for innovation.
But what makes the Raspberry Pi so special? For starters, it’s affordable, versatile, and easy to use. Plus, its open-source nature means you can customize it to suit your needs. And when you combine it with RemoteIoT, VPC, and SSH, you’ve got a setup that’s both powerful and secure.
Here’s a quick rundown of the Raspberry Pi’s key features:
Raspberry Pi Specifications
| Feature | Details |
|---|---|
| Processor | 1.8GHz 64-bit quad-core ARM Cortex-A72 |
| RAM | 4GB LPDDR4-3200 |
| Storage | MicroSD card slot |
| Connectivity | 2.4GHz and 5GHz Wi-Fi, Bluetooth 5.0 |
Integrating RemoteIoT, VPC, and SSH
Now that we’ve covered the individual components, let’s talk about how they all fit together. Integrating RemoteIoT, VPC, and SSH might sound intimidating, but with the right guidance, it’s actually quite straightforward.
Here’s a step-by-step guide to help you set up your secure remote access system:
- Create a VPC in your cloud provider’s dashboard
- Assign a private IP address to your Raspberry Pi
- Enable SSH on your Raspberry Pi
- Configure your firewall settings to allow SSH traffic
- Test your connection to ensure everything is working as expected
And there you have it—a secure and reliable setup that lets you access your Raspberry Pi from anywhere in the world.
Troubleshooting Tips
- Check your network settings if you can’t connect
- Ensure SSH is enabled on your Raspberry Pi
- Verify your firewall rules are correctly configured
Securing Your Connection
Security should always be at the top of your priority list. While RemoteIoT, VPC, and SSH provide a solid foundation, there are additional steps you can take to further secure your connection.
First, consider using SSH keys instead of passwords. Not only are they more secure, but they also eliminate the need to remember complex passwords. Additionally, enable two-factor authentication (2FA) to add an extra layer of protection.
Another important tip is to regularly update your software and firmware. This ensures that any vulnerabilities are patched, reducing the risk of unauthorized access.
Best Practices for Security
- Use SSH keys for authentication
- Enable two-factor authentication (2FA)
- Keep your software and firmware up to date
Common Issues and Solutions
No setup is without its challenges, and RemoteIoT VPC SSH Raspberry Pi is no exception. Here are some common issues you might encounter and how to resolve them:
- Can’t connect to Raspberry Pi via SSH: Double-check your IP address and ensure SSH is enabled.
- Slow connection speeds: Optimize your network settings and consider upgrading your internet plan.
- Unauthorized access attempts: Review your firewall rules and enable 2FA.
Remember, troubleshooting is all about patience and persistence. Don’t be discouraged if things don’t work perfectly the first time—keep trying, and you’ll get there.
Real-World Applications
Now that you’ve got the technical side down, let’s explore some real-world applications of RemoteIoT VPC SSH Raspberry Pi. From smart homes to industrial automation, the possibilities are endless.
For example, imagine being able to monitor and control your home’s energy consumption remotely. Or how about automating your manufacturing processes to improve efficiency? With RemoteIoT, VPC, and SSH, these scenarios are not only possible but also practical.
Here are a few examples of how this technology is being used in the real world:
- Smart home automation
- Industrial IoT applications
- Remote server management
Future Trends in RemoteIoT
As technology continues to evolve, so does the world of RemoteIoT. We’re seeing advancements in areas like edge computing, 5G connectivity, and AI-driven automation. These trends are set to transform the way we interact with IoT devices, making them even more powerful and accessible.
One exciting development is the rise of edge computing, which allows data to be processed closer to the source. This reduces latency and improves overall performance, making it ideal for applications that require real-time processing.
Another trend to watch is the integration of AI into IoT devices. By leveraging machine learning algorithms, devices can become smarter and more autonomous, reducing the need for human intervention.
Conclusion
Wrapping up, RemoteIoT VPC SSH Raspberry Pi is a powerful combination that offers unparalleled flexibility and security. Whether you’re a hobbyist or a professional developer, this setup has something to offer everyone.
By following the steps outlined in this guide, you can create a secure and reliable remote access system that meets your needs. Remember to prioritize security, regularly update your software, and don’t be afraid to experiment with new technologies.
So, what are you waiting for? Take action today by setting up your own RemoteIoT VPC SSH Raspberry Pi system. And don’t forget to share your experiences and tips in the comments below. Happy tinkering!