Are you diving into the world of IoT and wondering how SSH can transform your remote device management? Well, buckle up because we’re about to take you on a journey into the fascinating realm of SSH RemoteIoT examples. Whether you’re a tech enthusiast or a professional looking to enhance your IoT setup, this guide’s got you covered. So, what exactly is SSH RemoteIoT? Simply put, it’s a secure way to connect and control IoT devices remotely using SSH protocol. Let’s get started, shall we?
Before we jump into the nitty-gritty of SSH RemoteIoT, it’s important to understand why security matters in the Internet of Things ecosystem. With billions of connected devices out there, ensuring secure communication is no longer optional—it’s a necessity. And that’s where SSH comes in. It’s like having a personal bodyguard for your IoT devices, keeping unauthorized access at bay.
Now, if you’re wondering whether SSH RemoteIoT is worth the hype, the short answer is yes. Not only does it provide a secure channel for data transmission, but it also simplifies device management. From monitoring environmental sensors to controlling smart home appliances, SSH RemoteIoT opens up a world of possibilities. Let’s explore how it works and why it’s such a game-changer.
Table of Contents
- What is SSH RemoteIoT?
- Benefits of SSH RemoteIoT
- How SSH RemoteIoT Works
- Setting Up SSH RemoteIoT
- Common SSH RemoteIoT Examples
- Security Best Practices for SSH RemoteIoT
- Troubleshooting SSH RemoteIoT
- Advanced SSH RemoteIoT Configurations
- Real-World Applications of SSH RemoteIoT
- The Future of SSH RemoteIoT
What is SSH RemoteIoT?
SSH RemoteIoT refers to the use of the Secure Shell (SSH) protocol for managing and interacting with IoT devices remotely. Think of it as a secure tunnel that allows you to access your IoT devices from anywhere in the world. This is particularly useful for devices that are deployed in remote locations or require frequent monitoring and maintenance.
SSH, originally designed for secure remote access to servers, has proven to be an invaluable tool in the IoT space. It encrypts all communication between the client and the server, ensuring that sensitive data remains protected from prying eyes. With SSH RemoteIoT, you can execute commands, transfer files, and even set up automated processes—all from the comfort of your desk.
Why SSH is Ideal for IoT
Here are a few reasons why SSH is the go-to solution for secure IoT connectivity:
- Encryption: SSH uses strong encryption algorithms to secure data in transit.
- Authentication: It supports various authentication methods, including password-based and public key authentication.
- Portability: SSH is available on virtually every platform, making it easy to integrate with IoT devices.
- Scalability: Whether you’re managing a handful of devices or an entire fleet, SSH scales effortlessly.
Benefits of SSH RemoteIoT
There’s no denying that SSH RemoteIoT offers a plethora of advantages. Let’s break them down:
Enhanced Security
Security is the cornerstone of SSH RemoteIoT. By encrypting all communication, SSH ensures that sensitive data remains confidential. This is especially important in the IoT space, where devices often handle critical information such as health data, financial records, and more.
Remote Access Made Easy
Gone are the days when you had to physically access a device to make changes. With SSH RemoteIoT, you can connect to your devices from anywhere, as long as you have an internet connection. This not only saves time but also reduces the need for on-site visits.
Efficient Device Management
SSH RemoteIoT streamlines device management by allowing you to automate repetitive tasks. For instance, you can set up scripts to automatically update firmware, monitor system logs, and even reboot devices remotely.
How SSH RemoteIoT Works
So, how exactly does SSH RemoteIoT work? Let’s take a closer look at the process:
When you initiate an SSH connection, the client and server exchange cryptographic keys to establish a secure session. Once the connection is established, you can execute commands, transfer files, and interact with the device as if you were physically present.
Key Components of SSH RemoteIoT
- Client: The device or system you use to connect to the IoT device.
- Server: The IoT device itself, which acts as the SSH server.
- Encryption: The process of converting plain text into cipher text to protect data in transit.
- Authentication: The method used to verify the identity of the client and server.
Setting Up SSH RemoteIoT
Setting up SSH RemoteIoT is easier than you might think. Here’s a step-by-step guide to get you started:
Step 1: Install SSH Server on Your IoT Device
Most IoT devices come with SSH pre-installed, but if yours doesn’t, you’ll need to install an SSH server. Popular options include OpenSSH and Dropbear.
Step 2: Configure Firewall Settings
Make sure your firewall allows incoming SSH connections. By default, SSH uses port 22, but you can configure it to use a different port for added security.
Step 3: Connect to Your Device
Use an SSH client like PuTTY (for Windows) or the built-in SSH command in Linux and macOS to connect to your IoT device. Simply enter the device’s IP address and authentication credentials, and you’re good to go.
Common SSH RemoteIoT Examples
Now that you know how SSH RemoteIoT works, let’s explore some real-world examples:
Environmental Monitoring
Imagine you’re managing a network of weather sensors spread across a vast area. With SSH RemoteIoT, you can remotely access each sensor, retrieve data, and update configurations without ever leaving your office.
Smart Home Automation
SSH RemoteIoT can also be used to control smart home devices. From adjusting the thermostat to turning on the lights, everything can be done with a few simple commands.
Industrial IoT
In industrial settings, SSH RemoteIoT enables engineers to monitor and maintain machinery remotely. This is particularly useful for predictive maintenance, where issues can be identified and resolved before they escalate.
Security Best Practices for SSH RemoteIoT
While SSH RemoteIoT is inherently secure, there are a few best practices you should follow to further enhance security:
- Use Strong Passwords: Avoid using simple or easily guessable passwords.
- Enable Public Key Authentication: This eliminates the need for passwords and provides an additional layer of security.
- Disable Root Login: Restricting root access reduces the risk of unauthorized access.
- Monitor Logs: Regularly check SSH logs for suspicious activity.
Troubleshooting SSH RemoteIoT
Even with the best setup, issues can arise. Here are some common problems and their solutions:
Connection Refused
If you’re unable to establish a connection, check the following:
- Is the SSH server running on the device?
- Are firewall settings configured correctly?
- Is the IP address correct?
Authentication Failed
Authentication issues can occur due to incorrect credentials or misconfigured settings. Double-check your username and password, and ensure that public key authentication is properly set up.
Advanced SSH RemoteIoT Configurations
For those looking to take their SSH RemoteIoT setup to the next level, here are a few advanced configurations:
Port Forwarding
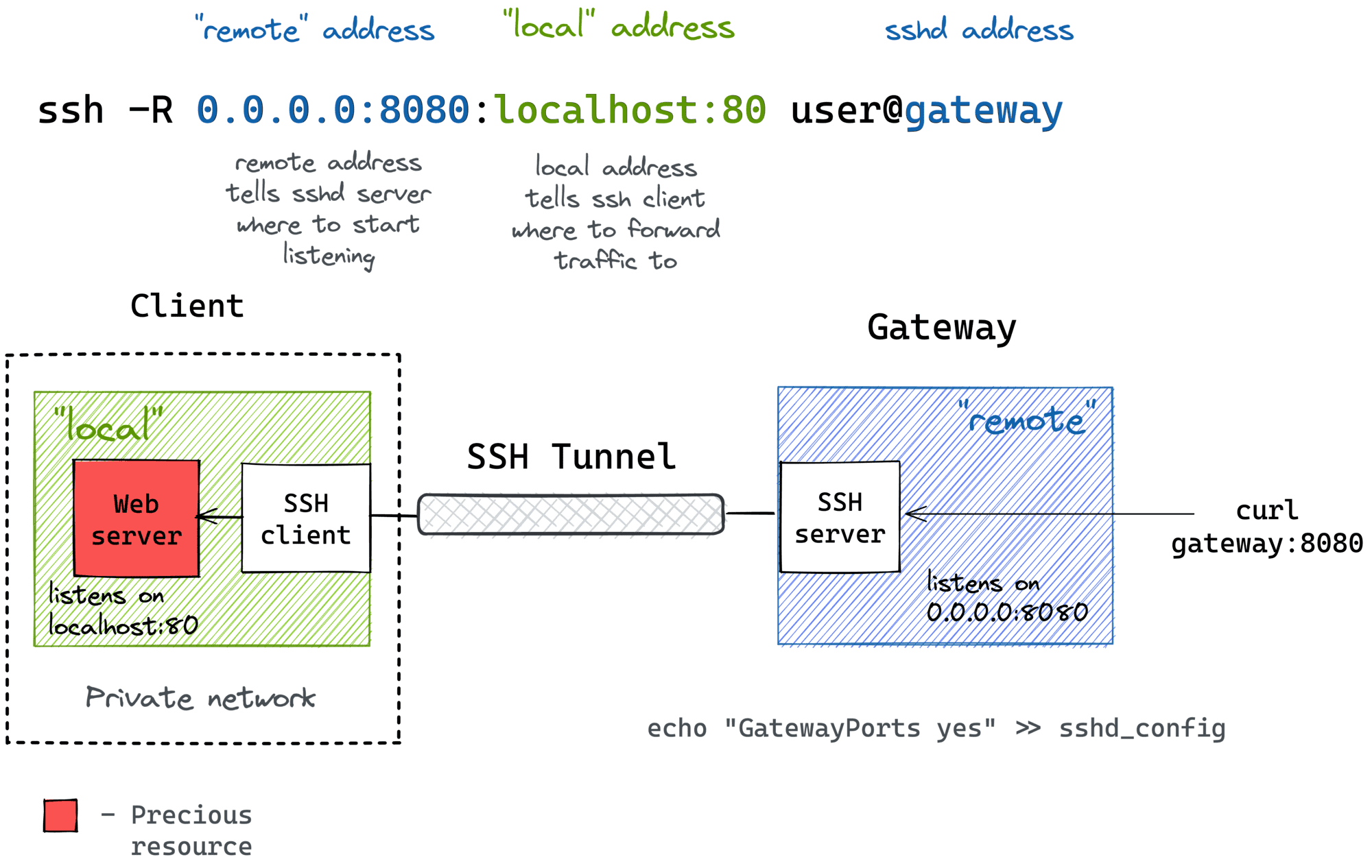
Port forwarding allows you to securely access services running on your IoT device from a remote location. This is particularly useful for web servers, databases, and other network services.
Tunneling
SSH tunneling can be used to bypass firewalls and access restricted resources. It’s like creating a secret passageway through which data can flow securely.
Real-World Applications of SSH RemoteIoT
SSH RemoteIoT is already being used in a variety of industries. Here are a few examples:
Agriculture
Farmers are using SSH RemoteIoT to monitor soil moisture levels, control irrigation systems, and optimize crop yields. This not only improves efficiency but also reduces water waste.
Healthcare
In healthcare, SSH RemoteIoT enables doctors and nurses to remotely monitor patients’ vital signs and adjust treatment plans in real-time. This is especially beneficial for patients living in remote areas.
Transportation
SSH RemoteIoT is also being used in the transportation industry to track vehicle performance, manage fleet operations, and improve safety. From buses to trains, SSH ensures that everything runs smoothly.
The Future of SSH RemoteIoT
As the IoT landscape continues to evolve, so too will SSH RemoteIoT. With advancements in quantum computing and artificial intelligence, we can expect even more secure and intelligent solutions in the future. Imagine a world where SSH automatically adapts to new threats and optimizes itself for peak performance. The possibilities are endless!
But for now, let’s focus on what we have and make the most of it. By leveraging SSH RemoteIoT, you can unlock the full potential of your IoT devices and take your projects to the next level.
Conclusion
In conclusion, SSH RemoteIoT is a powerful tool that offers secure, efficient, and scalable solutions for managing IoT devices remotely. From environmental monitoring to smart home automation, the applications are limitless. By following best practices and staying up-to-date with the latest trends, you can ensure that your SSH RemoteIoT setup remains secure and effective.
So, what are you waiting for? Dive into the world of SSH RemoteIoT and experience the future of IoT connectivity today. And don’t forget to share your thoughts and experiences in the comments below. Who knows, you might just inspire someone else to join the SSH RemoteIoT revolution!