Hey there, tech enthusiasts! Let’s dive straight into the heart of modern connectivity with a topic that's been making waves in the digital world. RemoteIoT SSH AWS Example is not just another buzzword; it's a game-changer for how we interact with devices remotely. Picture this: you're managing a network of IoT devices scattered across the globe, and you need a secure, efficient way to control them from your laptop. That's where this tech magic comes into play. It's like having a remote control for your entire IoT empire.
In today’s fast-paced tech landscape, understanding remote IoT management through SSH on AWS isn’t just an advantage—it’s a necessity. Whether you're a seasoned developer or just starting out, this guide is here to break down the complexities and make it all crystal clear. So, buckle up and get ready to explore the ins and outs of this powerful technology.
By the end of this article, you’ll have the tools and knowledge to set up your own remote IoT system using SSH on AWS. It’s time to take your tech skills to the next level and harness the full potential of what remote IoT can offer. Let’s get started, shall we?
Table of Contents
- Introduction to RemoteIoT SSH AWS Example
- What is SSH and Why Does It Matter?
- AWS Overview: Your Cloud Partner
- IoT Basics: Building the Foundation
- Setting Up RemoteIoT SSH on AWS
- Security Measures for RemoteIoT
- Example Projects: Putting It All Together
- Troubleshooting Common Issues
- Best Practices for RemoteIoT SSH AWS
- Future Trends in RemoteIoT SSH AWS
Introduction to RemoteIoT SSH AWS Example
So, what exactly is this RemoteIoT SSH AWS thing everyone’s talking about? Simply put, it’s the combination of three powerful technologies: IoT (Internet of Things), SSH (Secure Shell), and AWS (Amazon Web Services). These technologies work together to allow secure, remote access to IoT devices hosted on the cloud. It’s like having a superpower for managing your connected devices from anywhere in the world.
IoT devices are everywhere these days, from smart homes to industrial sensors. But managing them remotely can be a challenge, especially when security is a top priority. That’s where SSH comes in. SSH provides a secure channel over an unsecured network, making it perfect for controlling IoT devices remotely. And AWS? Well, it’s the backbone of the whole operation, offering scalable cloud infrastructure to host and manage your IoT fleet.
This setup isn’t just about convenience; it’s about efficiency and security. By leveraging SSH on AWS, you can ensure that your IoT devices are not only accessible but also protected from potential threats. This is crucial in today’s world, where cyberattacks are becoming increasingly sophisticated. Let’s explore more about how this works and why it matters.
What is SSH and Why Does It Matter?
Understanding SSH Basics
SSH, or Secure Shell, is like the secret handshake of the tech world. It’s a cryptographic network protocol that allows you to securely connect to a remote computer or device over an unsecured network. Think of it as a secure tunnel that protects your data as it travels from your device to the server. This is especially important when you’re dealing with sensitive information, like IoT device configurations.
SSH not only provides encryption for your data but also ensures authentication. This means that only authorized users can access your devices, preventing unauthorized access and potential security breaches. It’s like having a digital bouncer at the door of your IoT network, letting in only those who belong.
Why SSH is Essential for IoT
When it comes to IoT, security is paramount. These devices are often deployed in remote locations and can be accessed by multiple users. Without proper security measures, they become easy targets for hackers. SSH helps mitigate these risks by providing a secure way to manage and monitor your IoT devices.
Additionally, SSH supports various authentication methods, including password-based and public key authentication. Public key authentication is particularly useful for IoT devices, as it eliminates the need for passwords, reducing the risk of brute-force attacks. This makes SSH an ideal choice for securing IoT communications.
AWS Overview: Your Cloud Partner
Now, let’s talk about AWS. Amazon Web Services is the powerhouse behind many of today’s leading tech solutions. It offers a wide range of services, from compute power to storage, databases, and networking. For our purposes, AWS provides the perfect platform to host and manage IoT devices.
AWS IoT Core is one of the key services that make this possible. It allows you to connect millions of devices and process trillions of messages, all while maintaining security and scalability. With AWS, you can easily set up and manage your IoT infrastructure without worrying about the underlying hardware. It’s like having a personal IT team at your fingertips.
But AWS isn’t just about IoT. It also offers robust security features, including IAM (Identity and Access Management), which allows you to control who has access to your resources. This is crucial when you’re dealing with sensitive IoT data. AWS also provides monitoring and logging tools, making it easier to track and manage your IoT fleet.
IoT Basics: Building the Foundation
What is IoT?
IoT, or the Internet of Things, refers to the network of physical devices embedded with sensors, software, and connectivity, allowing them to exchange data with other devices and systems over the internet. These devices can range from simple sensors to complex industrial equipment. The goal of IoT is to create a smarter, more connected world, where devices can communicate and interact with each other seamlessly.
IoT has revolutionized many industries, from healthcare to manufacturing. In healthcare, IoT devices are used to monitor patients’ health in real time, providing valuable insights to doctors and caregivers. In manufacturing, IoT sensors help optimize production processes, reducing downtime and increasing efficiency.
Why IoT Matters for Remote Management
Remote management of IoT devices is becoming increasingly important as more devices are deployed in remote locations. Whether it’s a weather sensor on a mountaintop or a security camera in a remote warehouse, being able to manage these devices remotely can save time and money. It also allows for faster response times, as issues can be addressed without the need for physical intervention.
SSH on AWS provides the perfect solution for remote IoT management. It allows you to securely access and control your devices from anywhere in the world, using just a laptop or smartphone. This level of flexibility and control is essential in today’s fast-paced world, where time is money.
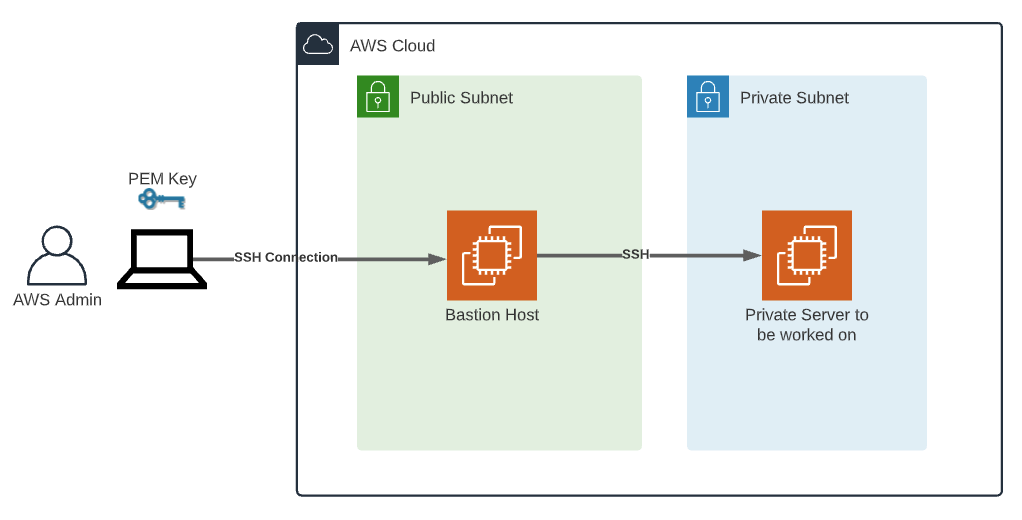
Setting Up RemoteIoT SSH on AWS
Step-by-Step Guide
Setting up RemoteIoT SSH on AWS may sound intimidating, but with the right guidance, it’s a straightforward process. Here’s a step-by-step guide to help you get started:
- Create an AWS Account: If you don’t already have one, sign up for an AWS account. It’s free to start, and you can explore many services without incurring any charges.
- Set Up an EC2 Instance: EC2 (Elastic Compute Cloud) is AWS’s virtual server offering. You’ll need to set up an EC2 instance to host your IoT devices. Choose an instance type that suits your needs and configure it with the necessary security settings.
- Install SSH Server: Once your EC2 instance is up and running, install an SSH server on it. This will allow you to connect to your instance securely from your local machine.
- Connect to Your Instance: Use an SSH client, like PuTTY or Terminal, to connect to your EC2 instance. You’ll need the public IP address of your instance and the key pair you created during setup.
- Deploy Your IoT Devices: Finally, deploy your IoT devices and configure them to communicate with your EC2 instance. This can be done using AWS IoT Core or other AWS services.
With these steps, you’ll have a fully functional RemoteIoT SSH setup on AWS. It’s like building your own digital fortress, where you can manage your IoT devices from anywhere in the world.
Security Measures for RemoteIoT
Best Practices for Securing Your IoT Devices
Security should always be a top priority when managing IoT devices. Here are some best practices to help you secure your RemoteIoT SSH setup:
- Use Strong Authentication: Implement public key authentication instead of password-based authentication. This reduces the risk of brute-force attacks and ensures only authorized users can access your devices.
- Limit Access: Restrict access to your EC2 instance by configuring security groups and network ACLs. This ensures that only trusted IP addresses can connect to your instance.
- Monitor Activity: Use AWS CloudTrail and CloudWatch to monitor activity on your instance. This allows you to detect and respond to suspicious behavior quickly.
- Keep Software Updated: Regularly update your SSH server and other software to patch any vulnerabilities. This ensures that your system is protected against the latest threats.
By following these best practices, you can significantly enhance the security of your RemoteIoT SSH setup, protecting your devices and data from potential threats.
Example Projects: Putting It All Together
Real-World Applications
Now that you have a solid understanding of RemoteIoT SSH on AWS, let’s look at some real-world applications. Here are a few example projects to inspire you:
- Smart Home Automation: Use SSH on AWS to control smart home devices, like lights, thermostats, and security systems, from anywhere in the world.
- Industrial IoT: Deploy IoT sensors in a factory to monitor equipment performance and optimize production processes.
- Environmental Monitoring: Set up a network of weather sensors to collect data on temperature, humidity, and other environmental factors, providing valuable insights for climate research.
These projects demonstrate the versatility and power of RemoteIoT SSH on AWS. Whether you’re building a smart home or monitoring the environment, this technology can help you achieve your goals.
Troubleshooting Common Issues
Solving Problems Quickly
Even with the best setup, issues can arise. Here are some common problems and how to solve them:
- Connection Issues: If you can’t connect to your EC2 instance, check your security groups and network ACLs to ensure that the necessary ports are open.
- Authentication Errors: If you’re having trouble authenticating, double-check your key pair and ensure that it matches the one on your instance.
- Performance Problems: If your instance is running slowly, consider upgrading to a larger instance type or optimizing your code to reduce resource usage.
By addressing these issues promptly, you can keep your RemoteIoT SSH setup running smoothly and efficiently.
Best Practices for RemoteIoT SSH AWS
Maximizing Efficiency and Security
To get the most out of your RemoteIoT SSH AWS setup, follow these best practices:
- Plan Your Architecture: Design your IoT infrastructure with scalability and security in mind. This will make it easier to manage as your fleet grows.
- Document Your Processes: Keep detailed documentation of your setup and configuration. This will help you troubleshoot issues and onboard new team members more easily.
- Stay Updated: Keep up with the latest trends and technologies in the IoT and cloud computing fields. This will ensure that your setup remains cutting-edge and relevant.
By following these best practices, you can maximize the efficiency and security of your RemoteIoT SSH AWS setup, ensuring that it meets your needs both now and in the future.
Future Trends in RemoteIoT SSH AWS
What’s Next for IoT and Cloud Computing?
The future of RemoteIoT SSH AWS looks bright, with many exciting trends on the horizon. Here are a few to watch out for:
- Edge Computing: As more devices are deployed at the edge of the network, edge