Ever wondered how you can connect to a device remotely and manage it from anywhere in the world? Well, SSH remote device is your answer. Whether you're a tech enthusiast, a developer, or just someone who wants to level up their tech skills, understanding SSH can be a game-changer. It's not just about accessing a machine remotely—it's about doing it securely, efficiently, and with confidence.
SSH, or Secure Shell, has been around for ages, but its importance continues to grow in today’s interconnected world. Think of it as a digital key that lets you unlock the door to your server or device, no matter where you are. But here's the kicker—it does it in a way that keeps prying eyes out. In this article, we'll dive deep into the world of SSH remote connections, exploring everything from the basics to advanced tips and tricks.
So, whether you're just starting out or you're looking to sharpen your skills, this guide has got you covered. We'll break down the complexities, highlight the best practices, and even throw in some real-world examples to help you get the most out of SSH remote device connections. Let's roll!
Before we dive in, here's a quick overview of what we'll be covering:
- What is SSH?
- How Does SSH Work?
- Benefits of Using SSH for Remote Access
- Setting Up SSH on Your Device
- Essential SSH Commands You Need to Know
- Securing Your SSH Connections
- Common SSH Issues and How to Fix Them
- Alternatives to SSH for Remote Connections
- Best Practices for Using SSH
- The Future of SSH and Remote Access
What is SSH?
Let's start with the basics. SSH, or Secure Shell, is a cryptographic network protocol designed for secure data communication over unsecured networks. It's like having a secret tunnel that only you and your device can access, keeping everything else out. When you're working with SSH remote device connections, you're essentially creating a secure link between your local machine and a remote server or device.
But why is it so important? In a world where cyber threats are on the rise, having a secure way to access your devices remotely is crucial. SSH encrypts all data that passes through it, making it nearly impossible for hackers to intercept or tamper with your information. It's not just about convenience—it's about security.
Why Use SSH Over Other Protocols?
There are plenty of ways to connect to a remote device, but SSH stands out for a few key reasons:
- Encryption: SSH uses strong encryption algorithms to protect your data.
- Authentication: It offers robust authentication methods, including password-based and public key authentication.
- Flexibility: SSH can be used for a wide range of tasks, from file transfers to remote command execution.
- Reliability: It's been around for decades and is trusted by millions of users worldwide.
When you're dealing with sensitive information, having a protocol that prioritizes security is a no-brainer. And that's exactly what SSH brings to the table.
How Does SSH Work?
Now that we know what SSH is, let's talk about how it works. At its core, SSH establishes a secure connection between two devices by using a combination of encryption, authentication, and data integrity checks. Here's a simplified breakdown of the process:
- Connection Initiation: When you initiate an SSH connection, your client sends a request to the remote server.
- Key Exchange: The server and client exchange cryptographic keys to establish a secure session.
- Authentication: The server verifies your identity using either a password or a public key.
- Encrypted Communication: Once authenticated, all communication between the client and server is encrypted.
It might sound complicated, but the beauty of SSH is that it handles all of this behind the scenes. All you need to do is enter a few commands, and the rest is taken care of for you.
The Role of Public and Private Keys
One of the most powerful features of SSH is its use of public and private keys for authentication. Here's how it works:
- Public Key: This is shared with the server and acts as a digital ID card.
- Private Key: This stays on your local machine and is used to prove your identity.
When you connect to a server using key-based authentication, the server checks the public key against your private key to verify that you are who you say you are. It's like having a digital handshake that ensures only authorized users can access the system.
Benefits of Using SSH for Remote Access
So, why should you use SSH for remote device connections? Here are just a few reasons:
- Security: SSH encrypts all data, making it nearly impossible for hackers to intercept or tamper with your information.
- Convenience: With SSH, you can access your devices from anywhere in the world, as long as you have an internet connection.
- Efficiency: SSH allows you to execute commands remotely, transfer files, and manage your devices without needing to be physically present.
- Scalability: Whether you're managing a single server or an entire network, SSH can handle it with ease.
These benefits make SSH an essential tool for anyone who needs to manage devices or servers remotely. Whether you're a developer, a system administrator, or just someone who wants to access their home server from work, SSH has got you covered.
Setting Up SSH on Your Device
Ready to get started with SSH? Setting it up is easier than you might think. Here's a step-by-step guide to help you get up and running:
Step 1: Install SSH
Most modern operating systems come with SSH pre-installed, but if yours doesn't, you can easily install it. For Linux and macOS users, SSH is usually available by default. Windows users can install it via the Windows Subsystem for Linux (WSL) or by using tools like PuTTY.
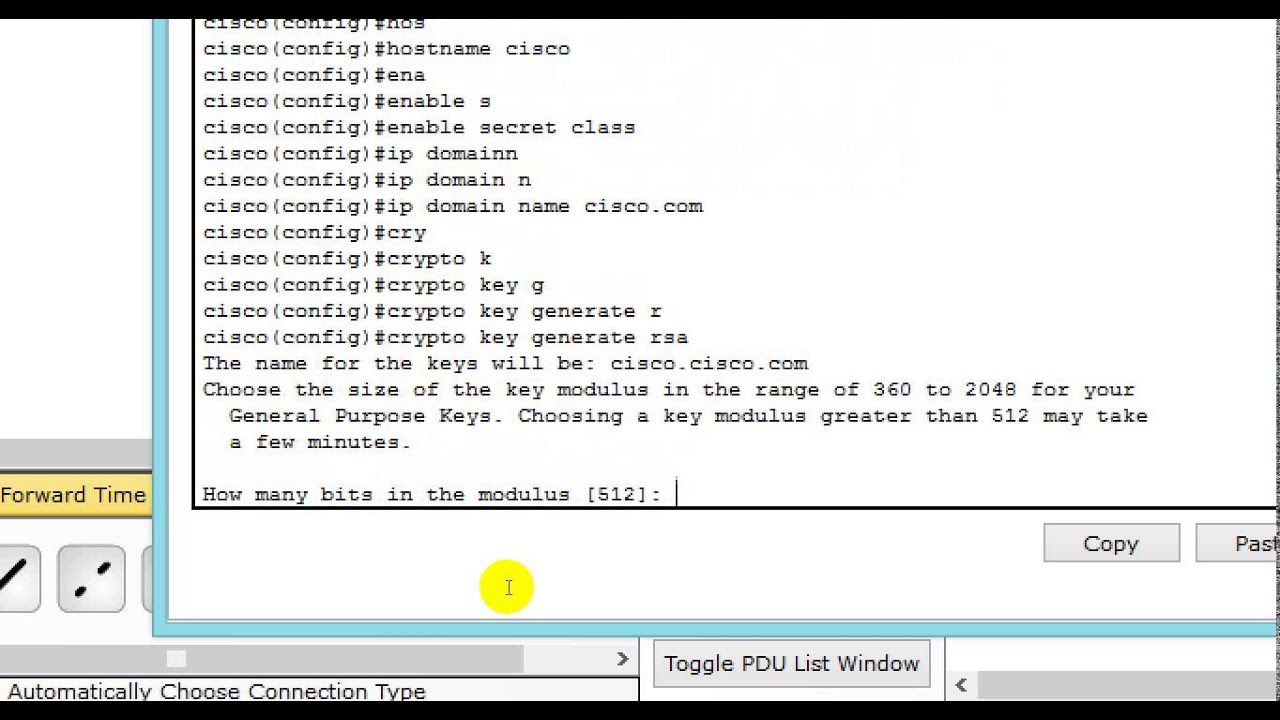
Step 2: Generate Keys
To set up key-based authentication, you'll need to generate a public and private key pair. Here's how:
- Open your terminal or command prompt.
- Run the command
ssh-keygen. - Follow the prompts to generate your keys.
Once your keys are generated, you'll need to add the public key to the server you want to connect to. This is usually done by adding it to the ~/.ssh/authorized_keys file on the server.
Step 3: Connect to the Server
With everything set up, connecting to your server is as simple as running the command ssh username@server_ip. Replace username with your username on the server and server_ip with the IP address of the server.
Essential SSH Commands You Need to Know
Once you're connected to your server, you'll want to know some basic SSH commands to help you navigate and manage your device. Here are a few essentials:
- ls: List files and directories.
- cd: Change directory.
- mkdir: Create a new directory.
- rm: Remove a file or directory.
- scp: Securely copy files between your local machine and the server.
These commands will help you get started with managing your server, but there's plenty more you can do with SSH. As you become more comfortable, you can explore advanced features like port forwarding and tunneling.
Securing Your SSH Connections
While SSH is inherently secure, there are still steps you can take to make your connections even more secure. Here are a few tips:
- Use Key-Based Authentication: Passwords can be guessed or brute-forced, but keys are much harder to crack.
- Disable Root Login: Allowing root login can be a security risk. Instead, use a regular user account and escalate privileges when needed.
- Change the Default Port: Attackers often target the default SSH port (22). Changing it to something less common can reduce the risk of attacks.
- Use a Firewall: Restrict access to your SSH port to only trusted IP addresses.
By following these best practices, you can significantly reduce the risk of unauthorized access to your devices.
Common SSH Issues and How to Fix Them
Even the best tools can have their hiccups. Here are a few common SSH issues and how to resolve them:
- Connection Refused: Make sure the SSH service is running on the server and that the port is open.
- Permission Denied: Double-check your keys and ensure that the permissions on the
~/.sshdirectory are set correctly. - Timeout Errors: Check your network connection and ensure that there are no firewalls blocking the connection.
If you're still having trouble, don't hesitate to consult the SSH logs on the server for more information.
Alternatives to SSH for Remote Connections
While SSH is the gold standard for remote connections, there are other options available. Here are a few alternatives:
- RDP (Remote Desktop Protocol): Best for graphical interfaces, but less secure than SSH.
- VNC (Virtual Network Computing): Another option for remote graphical access, but it lacks the encryption of SSH.
- Telnet: An older protocol that offers no encryption, making it unsuitable for sensitive data.
While these options have their uses, SSH remains the best choice for secure, text-based remote connections.
Best Practices for Using SSH
Here are a few best practices to keep in mind when using SSH:
- Regularly Update Your Keys: Rotate your keys periodically to reduce the risk of compromise.
- Monitor Your Logs: Keep an eye on your SSH logs for any suspicious activity.
- Limit Access: Restrict SSH access to only those who need it.
- Use Strong Passwords: If you must use password-based authentication, make sure your passwords are strong and unique.
By following these best practices, you can ensure that your SSH connections remain secure and reliable.
The Future of SSH and Remote Access
As technology continues to evolve, so too does the world of remote access. While SSH remains a cornerstone of secure connections, new tools and technologies are emerging that could change the game. From quantum encryption to AI-driven security solutions, the future of remote access is exciting and full of possibilities.
But one thing is certain—SSH will continue to play a vital role in securing our digital world. Whether you're managing servers, accessing devices remotely, or simply learning the ropes, SSH is a skill that will serve you well for years to come.
Kesimpulan
In conclusion, mastering SSH remote device connections is an essential skill for anyone working in the tech industry—or anyone who wants to take their tech skills to the next level. From understanding the basics to implementing best practices, this guide has provided you with everything you need to get started and succeed with SSH.
So